OK, now the failure is here:
https://linkdcvp.linkstream.tv:8443/hls/content/entry/data/0/1/content/entry/data/0/0/0_l1anrkhv_0_ameuirkh_2.mp4/index.m3u8
Which leads to:
HTTP/1.1 404 Not Found
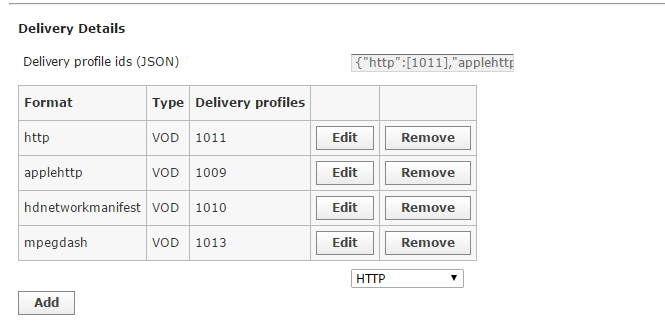
Let me explain again how the default HLS delivery profile works and then you can make sure whatever you’ve overridden works in a similar way.
I’m pasting sample URLs from my own host: jessex.
First call of interest from the player’s end is the playManifest one:
http://jessex/p/102/sp/10200/playManifest/entryId/0_22bqymiq/flavorIds/0_uqs3qqh6,0_e0lgehpv,0_ip2l71zy,0_04kzo9dh/format/applehttp/protocol/http/a.m3u8
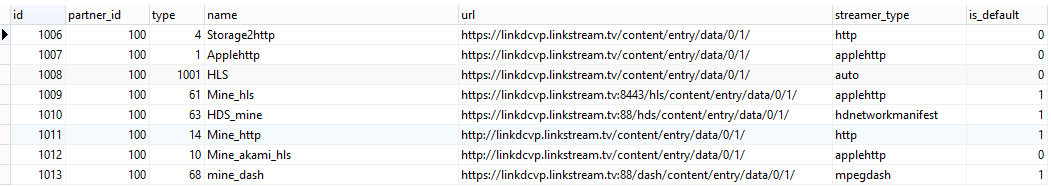
When using the default HLS profile [ID 1001 in the delivery_profile table], this will lead to /opt/kaltura/app/alpha/lib/model/DeliveryProfileVodPackagerHls.php
If look at this file, you’ll see the DeliveryProfileVodPackagerHls class extends the DeliveryProfileAppleHttp, which in turn extends DeliveryProfileVod, where you will find the getBaseUrl() function.
Long flow short, doGetFlavorAssetUrl() in /opt/kaltura/app/alpha/lib/model/DeliveryProfileVodPackagerHls.php will return http://jessex:88/hls/p/102/sp/10200/serveFlavor/entryId/0_22bqymiq/v/2/flavorId/0_uqs3qqh6/name/a.mp4/index.m3u8, this request will be made to the Nginx. Now, if you look at the Nginx conf [/opt/kaltura/nginx/conf/kaltura.conf or /etc/nginx/conf.d/kaltura.conf depending on whether this is the RPM or deb package], you’ll find:
# serve flavor HLS
location ~ ^/hls/p/\d+/(sp/\d+/)?serveFlavor/ {
vod hls;
vod_bootstrap_segment_durations 2000;
vod_bootstrap_segment_durations 2000;
vod_bootstrap_segment_durations 2000;
vod_bootstrap_segment_durations 4000;
add_header Last-Modified "Sun, 19 Nov 2000 08:52:00 GMT";
add_header Access-Control-Allow-Headers "*";
add_header Access-Control-Expose-Headers "Server,range,Content-Length,Content-Range";
add_header Access-Control-Allow-Methods "GET, HEAD, OPTIONS";
add_header Access-Control-Allow-Origin "*";
expires 100d;
}
So, not sure what you’ve done in your custom delivery profile class but I hope this will help you understand what you need to change.
Also, note that with curl you still get:
curl: (60) SSL certificate problem: unable to get local issuer certificate
More details here: http://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.
When making the request from a browser, this is forgiven but still, I recommend you fix it by including the CA cert in the file you set the Nginx ssl_certificate directive to in ssl.conf.